Violent Rapberry Pi Zero: Configuration - Part 1
As it’s possible to configure the USB port of the Raspberry Pi Zero as an Ethernet (also HID, hard drive) device, we will try to imitate the USB Armory attacks in a cheaper open-source hardware.
Objectives Part 1: Configure the Pi to enable the USB Ethernet and connect trough SSH.
We will follow the instructions to modify the image:
- Flash Raspbian Jessie onto the SD card.
- In the boot partition:
- config.txt -(Add)–> dtoverlay=dwc2
- cmdline.txt -(Add after rootwait)–> modules-load=dwc2,g_ether
In this case we will connect through the serial port to the Raspberry Pi to check the IP, as we can not SSH into it using the raspberrypi.local address. (and because we can :D )
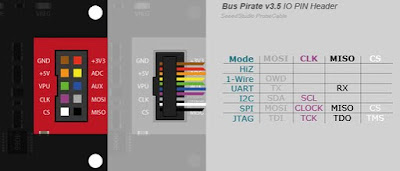
We will connect with the Bus Pirate tool to the UART port.
Check the color of the UART wires (gray and black):
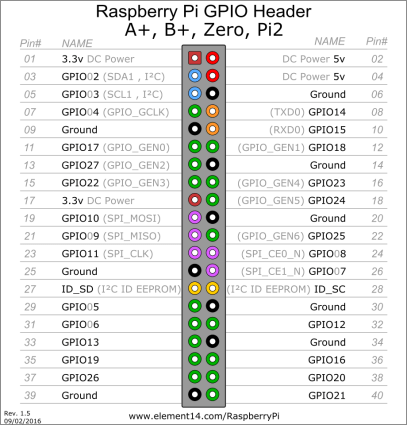
Check the Pins of the UART protocol (GPIO 14 and 15):
Connection resume:
- Bus Pirate Red wire –> RPI Pin #3 (3.3V)
- Bus Pirate Black wire –> RPI Pin #8 (GPIO14)
- Bus Pirate Gray wire –> RPI Pin #10 (GPIO15)
- Bus Pirate Brown wire –> RPI Pin #34 (GND)
UART connection through Bus Pirate and SSH through USB0 interface:
Actually the simplest way is to edit the dhcpcd.conf file after flashing the SD:
Add the static IP configuration in the Raspberry Pi (/etc/dhcpcd.conf): interface usb0 static ip_address=169.254.64.64
Add the static IP configuration in the host: 169.254.64.65 255.255.0.0 169.254.64.64